Build our psychological resistance against online misinformation

Training Kits
How to verify internet resources through simple protocols?

Overview
This module provides steps to verify information that is accessible to all.
Unlike similar information found in newspapers or television broadcasts, information available on the Internet is not regulated for quality or accuracy; therefore, it is particularly important for the individual Internet user to evaluate the resource or information. Keep in mind that almost anyone can publish anything they wish on the Web. It is often difficult to determine authorship of web sources, and even if the author is listed, he or she may not always represent him or herself honestly, or he or she may represent opinions as facts. The goal of this module is to show that disinformation is a common process and verification of information is easy and within everyone’s reach.
Target group
Adults and youngsters in formal and non-formal training settings
Evaluation method
Reflection and
Practical activities
Materials
▶ Paper and pens, Tape, Highlighters, Markers
▶ Computer and screen for showing video examples
▶ Link: https://www.getbadnews.com/en/
Training Objectives - LOM
Question the sources, and verify the credibility and veracity of the information found.
Develop skills in finding, selecting and interpreting information
Apply different protocols to verify the credibility of the available internet resources and assess the reliability of a source
Compare the different existing proposals to verify the credibility of the available internet resources
Summarize different proposals to verify internet resources
Demonstrate how to verify internet resources via different protocols
Concepts & Definitions
Primary source
First-hand evidence giving you direct access to your research topic (e.g.: Empirical or statistical results)
Secondary source
Second-hand information that analyses, describes, or evaluates primary sources (e.g.: book)
Tertiary Source
Sources that identify, index, or consolidate primary and secondary sources (e.g.: encyclopaedia)
Protocol
A system of rules that explain the correct conduct and procedures to be followed in formal situations.
Verification
a process that takes newsworthy information and checks its credibility and reliability before it is published or broadcast as news
Click restraint
A simple strategy that involves resisting the urge to immediately click on the first search result. Instead, students scan the results to make a more informed choice about where to go first
ABC of source evaluation
There are many protocols and devices you can use to evaluate the credibility of information.
One protocol is as easy as ABCDE: A=Author: Who is the author or creator of the information?, B=Bias: What is the author’s bias?, C=Content: Examine the content for clues about the source’s credibility, D= Date: What is the date of publication?, E=Evidence: What evidence does the author/creator provide to support her/his claims?
CRAAP Test
The CRAAP Test is a protocol that provides a list of questions to help you evaluate the information you find. Evaluation Criteria:
Currency: The timeliness of the information. Relevance: The importance of the information for your needs. Authority: The source of the information. Accuracy: The reliability, truthfulness, and correctness of the content. Purpose: The reason the information exists.
E.S.C.A.P.E. Junk News
Simple protocol to help you check online news and find out if they are reliable. Evaluation Criteria:
Evidence: Do the facts hold up?, Source: Who made this, and can I trust them?, Context: What’s the big picture?, Audience: Who is the intended audience?, Purpose: Why was this made?, Execution: How is this information presented?
SIFT Model
Protocol based on a a series of actions one can take in order to determine the validity and reliability of claims and sources on the web. Based on “Four Moves”:
Stop
Investigate the Source
Find better Coverage.
Trace Claims, quotes and media to the original context
Method 1
Icebreaker and game for building psychological resistance against online misinformation.
Warm up – 15-20 min
Arrange chairs in a circle, if possible.
The trainer presents him/herself and the aims of the session: each participant presents him/herself telling 3 facts about themselves and 1 is a lie.
Give an example by introducing yourself and telling a lie and asking the participants to try to find out which one is the lie (Example: My name is Leonard, I practice scuba diving and I am allergic to cats. You give 30 seconds to the audience to say which one is the lie and then you explain which one)

Introduction – 5 min
Introduction: what we can find out there. There are many types information on the internet. And not all of them contain credible information. As examples of the different websites we can find:
» Personal sites and blogs are usually maintained by individuals for their own enjoyment. Although the author of a blog may have authority in his or her field, blog posts lack the indicators of scholarly publishing, such as peer review.
» Commercial websites are maintained by for-profit companies. It’s important to remember this bias when assessing their credibility.
» Informational websites are maintained by organizations or institutions for the purpose of sharing research or other information. You’ll need to think about what authority these sources have, in the real world as well as online.
» News and journalism online comes from a variety of sources, some more reliable than others…
The reopening took place on 3 September 2015, passing to the management of the University of Alaska Fairbanks and open leases and partnerships to cover the costs.
It was and still is at the centre of several conspiracy theories, e.g. the ‘fireball’ spotted in the Black Sea after the 1999 earthquake in Istanbul, when the centre was in operation.
In Module 1 we have been learning about the different kinds of information and we are already aware that some information we find out there can be false… and has been created and shared to deliberately cause harm.
We propose you now to play a game. By playing this game you will build your psychological resistance against online misinformation.
The game draws on the theory of psychological inoculation: just as exposure to a weakened strain of a pathogen triggers the production of antibodies to cultivate immunity against a virus, the same can reasonably be achieved with information.
Specifically, the game forewarns and exposes players to severely weakened doses of the strategies that are used in the production of fake news to stimulate the production ‘mental antibodies’ against misinformation.
Activity 1
BAD NEWS GAME
In the Bad News Game, you take on the role of fake news-monger: you have to drop all pretence of ethics and choose a path that builds your persona as an unscrupulous media magnate. But keep an eye on your ‘followers’ and ‘credibility’ meters. Your task is to get as many followers as you can while slowly building up fake credibility as a news site. But watch out: you lose if you tell obvious lies or disappoint your supporters!
The goal of the game is to expose the tactics and manipulation techniques that are used to mislead people and build up a following. Bad News works as a psychological “vaccine” against disinformation: playing it builds cognitive resistance against common forms of manipulation that you may encounter online.
Scientists who worked on the development of this game found that playing Bad News improves people’s ability to spot manipulation techniques in social media posts, increases their confidence in spotting such techniques, and reduces their willingness to share manipulative content with people in their network.
You can read more about the science behind the game HERE.
PLAY THE GAME: https://www.getbadnews.com/en/
Debate after Activity 1 BAD NEWS GAME– 15 min
What did you like most and least about the game?
What did you learn?
Was it useful to create “antibodies for misinformation”?
Do you believe that if enough people are “vaccinated” and have developed psychological antibodies, misinformation is less likely to be spread?
After playing the game: how can we respond to new misinformation methods and narratives?
Method 2
Internet Research, & small groups discussion: Types of sources and online Internet sources protocols
In this part of the learning:
- We will present the different types of sources as an introduction
- We will also present what a protocol is, what verification is about and why we needs as users of information, verification protocols
- Then the trainer will ask learners to separate in 3-4 groups of 4-5 person maximum and ask them to research on the internet: find 3 different online Internet source Verification protocols (asking them to describe the order of the protocols in the browser) and present them shortly.
- Presentation of results: Each group will be asked to inform about their protocols and say their number in the list of the browser using a screenshot.
- All the learners will debate results in a plenary discussion
What is a protocol:
A system of rules that explain the correct conduct and procedures to be followed in formal situations.
What is verification:
related to information, verification is a process that takes newsworthy information and checks its credibility and reliability before it is published or broadcast as news
Why do we need, as users of information, verification protocols?
It is important to critically evaluate sources because using credible/reliable sources makes you a more informed user. Think about unreliable sources as pollutants to your credibility, if you include unreliable sources when you use social networks, your work could lose credibility as a result.
Activity 2
Available online Internet sources protocols
- The trainer will ask learners to separate in 3-4 groups of 4-5 person maximum with 1 computer or smart phone per group
- The task for the groups is to find 3 different online Internet sources protocols
- In short, the learners are asked to:
- select a spokesperson per group,
- search on the internet (as example, they can use the wording: online Internet sources protocols),
- list the order of the protocols that are found in the browser (by order of appearance) and
- describe them shortly.

- Presentation of results: Each group will be asked to inform about their protocols and say their number in the list of the browser using a screenshot.
- Debate and closing:
- Was the order of the listed protocols similar in all the groups involved?
- Did you consider the listing and the order as suitable?
- How many pages of results did you check?
Activity 3
How to Find Better Information Online: Click Restraint
In this part of the learning:
- We will present what click restraint is, including a video
- The trainer will ask learners to separate in 3-4 groups of 4-5 person maximum with 1 computer or smart phone per group. The trainer will ask again learners to search 3 different online Internet sources protocols (now using the click restraint technique) and describe them shortly. Make a list of the protocols THEY FOUND MORE INTERESTING and describe them.
- Presentation of results: Each group will be asked to inform about their protocols and say their number in the list of the browser using a screenshot.
- All the learners will debate results in a plenary discussion
As activities 2 and 3 are linked: they can be finalized with a closing “reflection” activity in which learners are asked to finish the sentence (It was difficult ….. I learned …. It was interesting to know that….. I was surprised when…. Now I will… )

When we have a question or are searching for sources, we likely turn to a search engine to help us find answers.
We often click on the first result, perhaps because sifting through all the results takes time, or because we assume the first result is the most trustworthy.
But the first result is not always the best place to start.
Spending a little more time scanning search results can help us make a more informed choice about where to go first.
"Click restraint"
“Click restraint” refers to the ability to restrain yourself from clicking on the very first results you get from a search engine: you should not immediately click on the first search results. Instead you may scan a search results page, looking at things like the title, source description, and featured sections, before deciding what sources to examine. This helps you to get a fuller picture of the coverage available on that source, as well as to look for sources that don’t come from the original source.
Watch the video:

- The trainer will ask learners to separate in 3-4 groups of 4-5 person maximum with 1 computer or smart phone per group
- Trainer will ask learners to search 3 different online Internet sources protocols (now using the click restraint technique) and describe them shortly. That is, the learners are asked to:
- select a spokesperson per group,
- search on the internet (again, using use the wording: online Internet sources protocols),
- Make a list of the protocols THEY FOUND MORE INTERESTING and
- describe them shortly.
- Presentation of results: Each group will be asked to inform about their results referring to 3 protocols they have identified as the most suitable.
- Debate:
- Was the 3 selected protocols similar in all the groups involved?
- Dis you consider the selected protocols suitable?
- How many pages of results did the groups check?
- Closing: When we want to find out more about a topic or question, most of us turn to Google. But open Internet searches routinely turn up contradictory results that mix fact with falsehood. Making sense of search results is more challenging than it may seem. Activities 2 and 3 are linked: thy first were asked to report about the order of appearance in the browser and afterwards, knowing better about click restraint, to assess their ability to wade through information to find sources, evidence, and arguments that they can trust.
Tip fro trainers: these 2 activities can be finalised with a “Reflection” activity in which learners are asked to finish the sentence:
It was difficult …..
I learned ….
It was interesting to know that…..
I was surprised when….
Now I want to…
Activity 4
Presentation of protocols and SIFT model in practice (case study)
In this part of the learning:
- We will present different models for verifying internet sources: the ABC source of information, the CRAAP test, the ESCAPE junk News and the SIFT model
- We will also introduce a Case Study with a link to a news applying the SIFT model
- All the learners will debate results in a plenary discussion
Introduction - ABCs of Source Evaluation
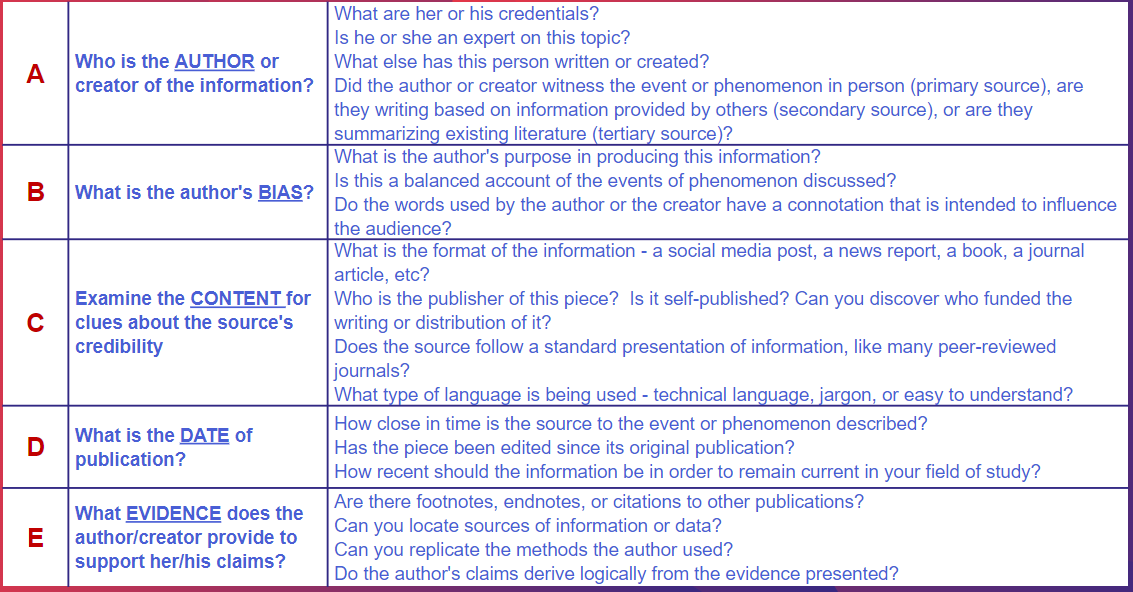
The CRAAP Test is a list of questions to help you evaluate the information you find. Different criteria will be more or less important depending on your situation or need.
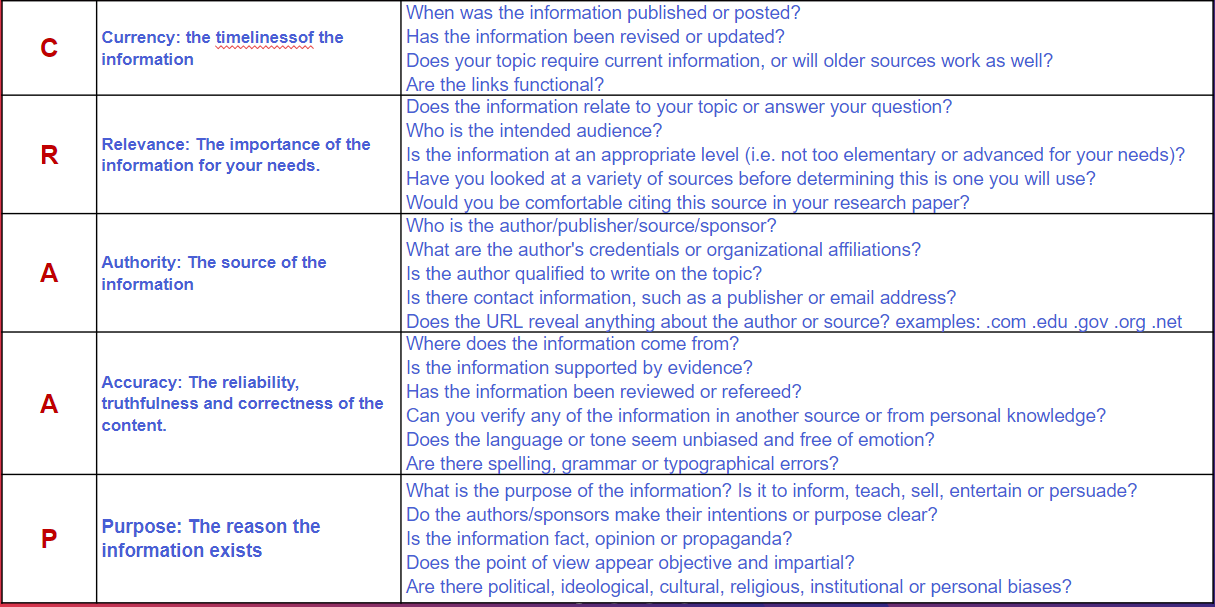
E.S.C.A.P.E - a handy acronym to help them remember six key concepts for evaluating information (Evidence, Source, Context, Audience, Purpose, Execution)
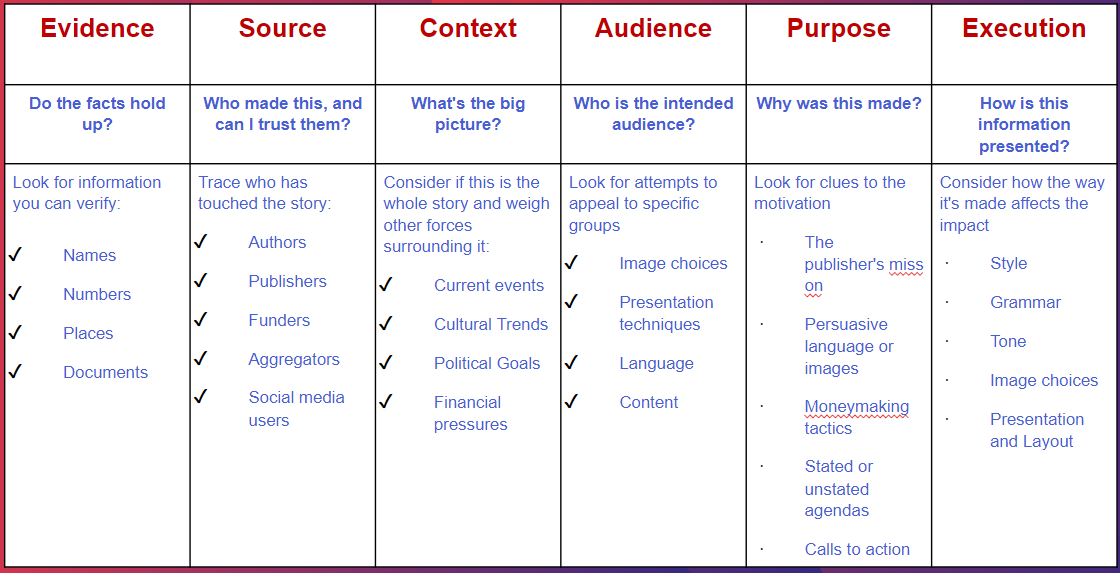
SIFT MODEL: an evaluation method designed by Mike Caulfield
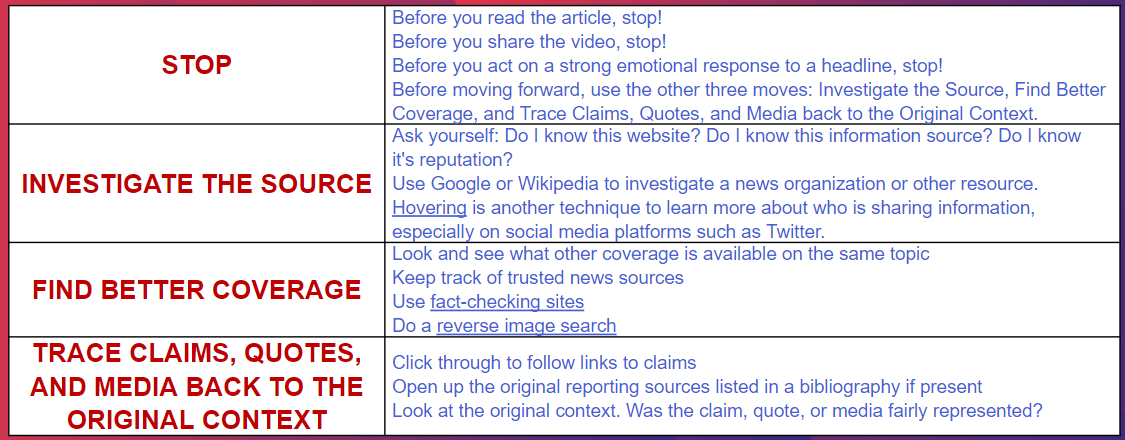
Case study 1
Let’s apply the SIFT model
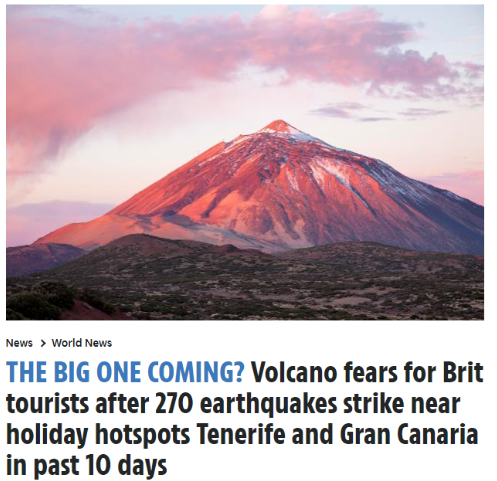
British media published an article about a possible “mega eruption” of the Teide volcano on the Canary island of Tenerife (Spain). The headlines included information such as “Tenerife volcano alert: Shock as 270 earthquakes hit Brit holiday favourite Canary Islands” and “Earthquakes near Tenerife and Gran Canaria spark fears of volcanic eruption.”
The stories included some images.
TAKE A LOOK TO THE ARTICLE DIRECTLY AT:
https://www.thesun.co.uk/news/6236222/volcano-earthquakes-spain-tenerife-gran-canaria-mount-teide/
Do I know this website?
Do I know this information source?
Do I know it’s reputation?
Use Google or Wikipedia to investigate a news organization or other resource (for example, publications in Spain about it – you can use Google translate. )
Click through to follow links to claims. Open up the original reporting sources (IF ANY). Look at the original context: Was the claim, quote, or media fairly represented?
Closing the activity – 10 min
Summary: British media outlets have warned their readers of a possible “mega eruption” of the Teide volcano on the Canary island of Tenerife. Alarmist headlines included “Tenerife volcano alert: Shock as 270 earthquakes hit Brit holiday favorite Canary Islands” and “Earthquakes near Tenerife and Gran Canaria spark fears of volcanic eruption.”…
But these warnings were not repeated by Spanish media, first because there were never 270 earthquakes in the Canary Islands – it was an invention of the British tabloids – and secondly, because there is no threat of an eruption at Mount Teide.
Reflection:
- Did you find the SIFT model easy to apply?
- Will you use it from now on?
END OF MODULE
